
4.9 (450) · $ 134.00 · In stock
Description

What is Application Allowlisting?
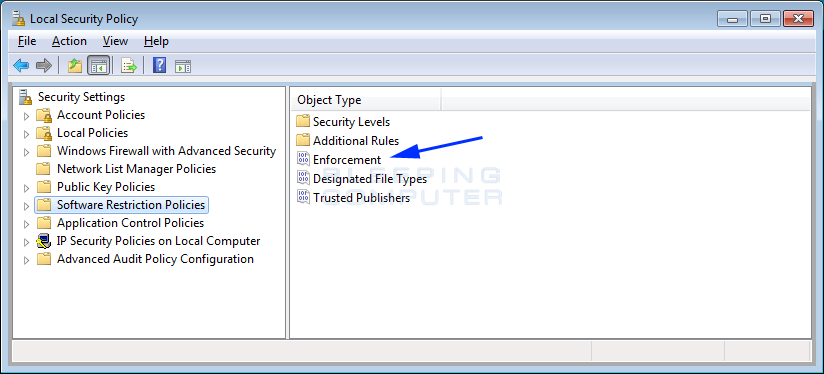
How to create an Application Whitelist Policy in Windows

How to Improve Cloud Security
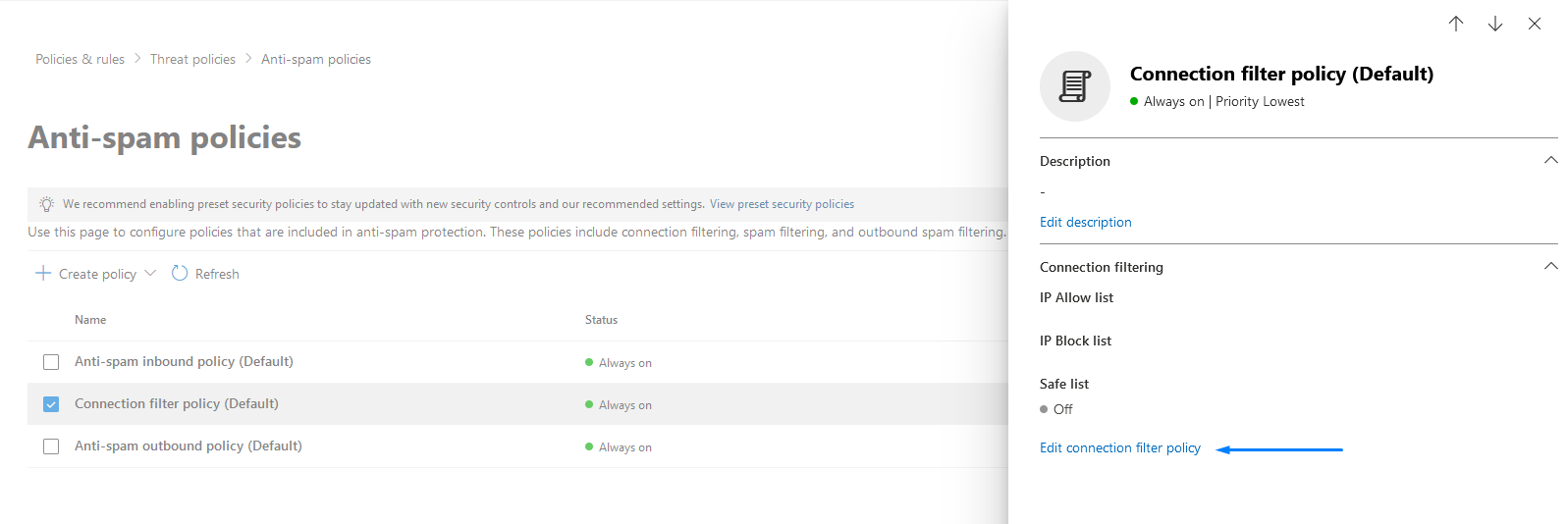
Whitelisting for Office 365

What Is Whitelisting And How To Implement It? - Great Learning

Application Whitelisting Enforcement during Process Creation
Deploying a whitelist Software Restriction Policy to prevent Cryptolocker and more - Windows Forum

Everything You Always Wanted to Know About Restricting Token Transfers But Were Afraid to Ask, by Pablo Ruiz

Whitelisting Azure IPs' in Snowflake, by Shankar Narayanan SGS, Snowflake

What is a Security Whitelist? - Coralogix

What Is Whitelisting and How Should You Implement It?
Operationalizing IP Allow Lists for Cloud Environments - Netskope